This Page includes more info about different cloud providers
This is the multi-page printable view of this section. Click here to print.
Cloud Provider
- 1: Amazon Web Services
- 2: Azure
- 3: Kind
1 - Amazon Web Services
AWS integration for Self-Managed and Managed Kubernetes Clusters
Caution
AWS credentials are required to access clusters. These credentials are sensitive information and must be kept secure.Authentication Methods
Command Line Interface
Use the ksctl credential manager:
ksctl configure cloud
Available Cluster Types
Self-Managed Clusters
Self-managed clusters with the following components:
- Distributed etcd database instances
- HAProxy load balancer for control plane high availability
- Multiple control plane nodes
- Worker nodes
Choose between two bootstrap options:
- k3s (lightweight Kubernetes distribution)
- kubeadm (official Kubernetes bootstrap tool)
Amazon EKS (Managed Clusters)
Elastic Kubernetes Service deployment with automated:
- IAM role creation and management
- Control plane setup
- Node group configuration
IAM Configuration
For each cluster, ksctl creates two roles:
ksctl-<clustername>-wp-role: Manages node pool permissionsksctl-<clustername>-cp-role: Handles control plane access
Required IAM Policies
- Custom IAM Role Access Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor6",
"Effect": "Allow",
"Action": [
"iam:CreateInstanceProfile",
"iam:DeleteInstanceProfile",
"iam:GetRole",
"iam:GetInstanceProfile",
"iam:RemoveRoleFromInstanceProfile",
"iam:CreateRole",
"iam:DeleteRole",
"iam:AttachRolePolicy",
"iam:PutRolePolicy",
"iam:ListInstanceProfiles",
"iam:AddRoleToInstanceProfile",
"iam:ListInstanceProfilesForRole",
"iam:PassRole",
"iam:CreateServiceLinkedRole",
"iam:DetachRolePolicy",
"iam:DeleteRolePolicy",
"iam:DeleteServiceLinkedRole",
"iam:GetRolePolicy",
"iam:SetSecurityTokenServicePreferences"
],
"Resource": [
"arn:aws:iam::*:role/ksctl-*",
"arn:aws:iam::*:instance-profile/*"
]
}
]
}
- Custom EKS Access Policy
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"eks:ListNodegroups",
"eks:ListClusters",
"eks:*"
],
"Resource": "*"
}
]
}
- AWS Managed Policies Required
- AmazonEC2FullAccess
- IAMReadOnlyAccess
Kubeconfig Authentication
After switching to an AWS cluster using:
ksctl switch aws --name here-you-go --region us-east-1
The generated kubeconfig uses AWS STS tokens which expire after 15 minutes. When you encounter authentication errors, simply run the switch command again to refresh the credentials.
Looking for CLI Commands?
All CLI commands mentioned in this documentation have detailed explanations in our command reference guide.
CLI Reference
👉 Check out our comprehensive CLI Commands Reference for:
- Detailed command syntax
- Usage examples
- Available options and flags
- Common use cases
2 - Azure
Azure support for Self-Managed and Managed Kubernetes Clusters
Caution
Azure credentials are required to access clusters. These credentials are sensitive information and must be kept secure.Azure Credential Requirements
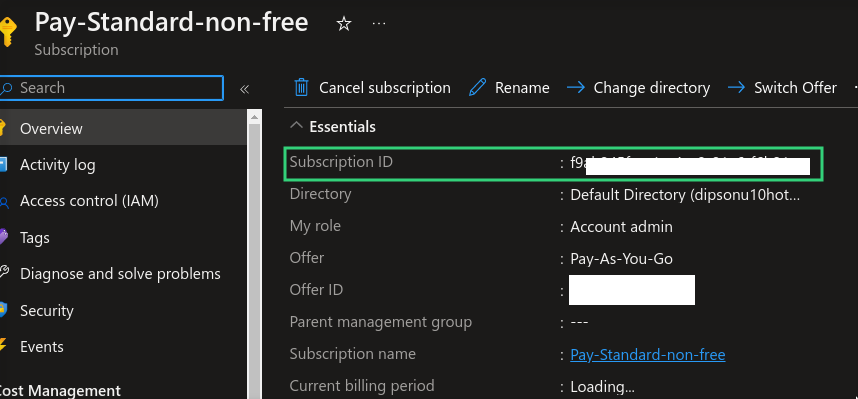
Subscription ID
Your Azure subscription identifier can be found in your subscription details.
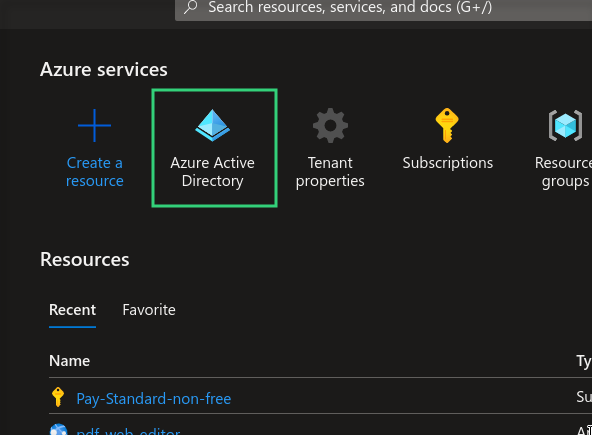
Tenant ID
Located in the Azure Dashboard, which provides access to all required credentials.
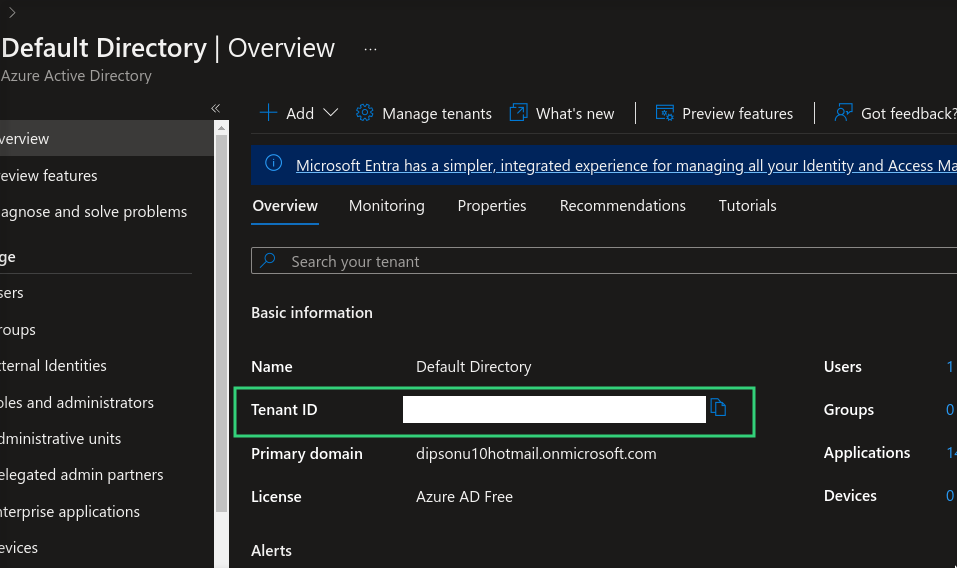
To locate your Tenant ID:
Client ID (Application ID)
Represents the identifier of your registered application.
Steps to create:
- Navigate to App Registrations
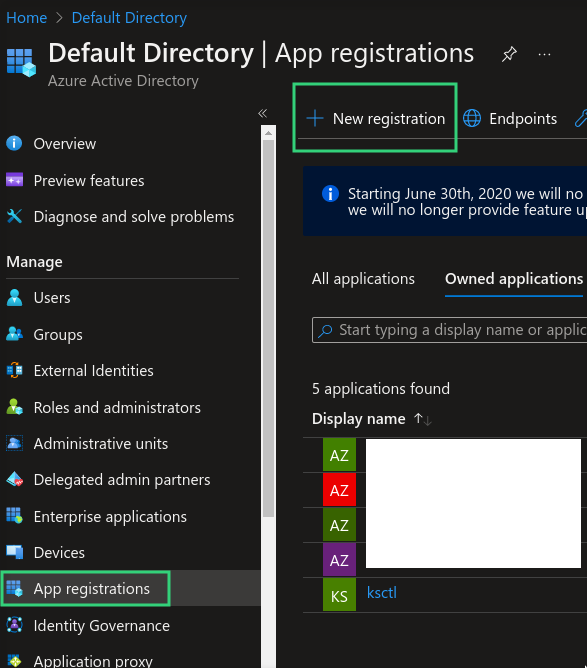
Register a new application
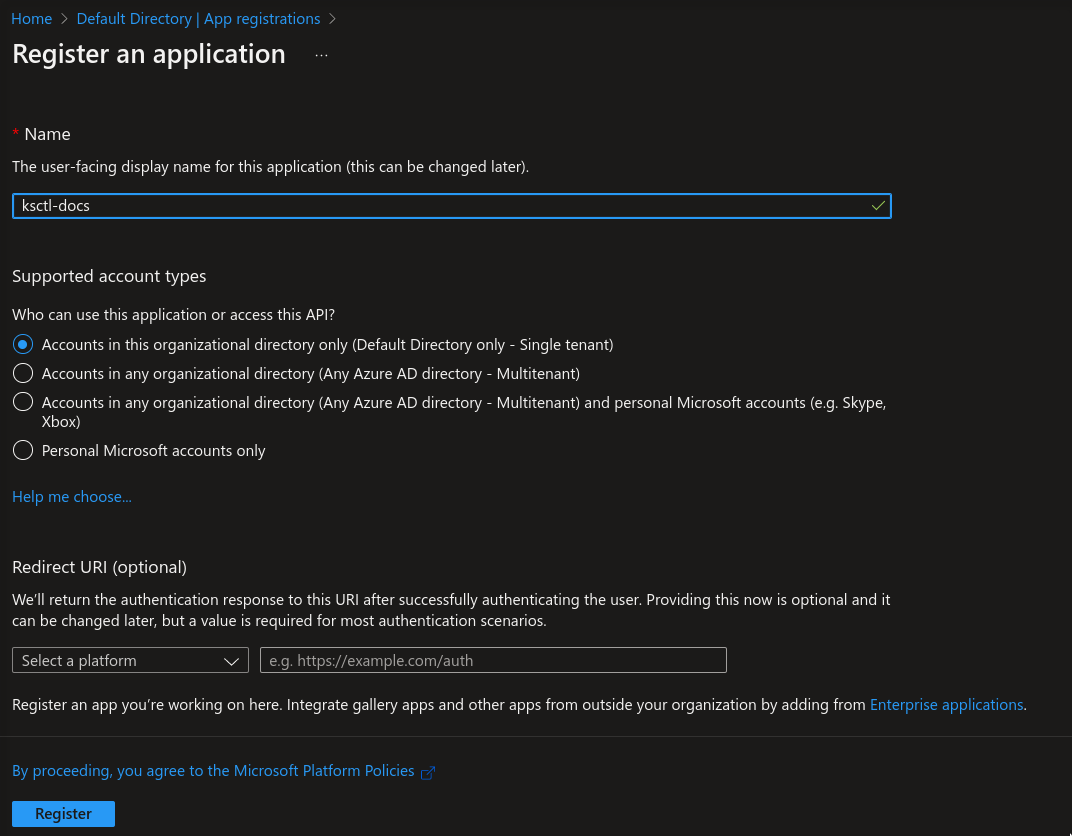
Obtain the Client ID
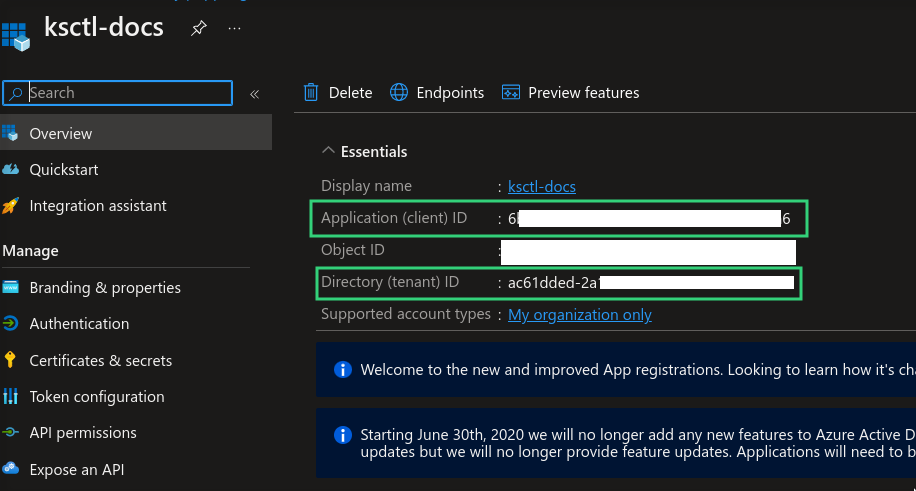
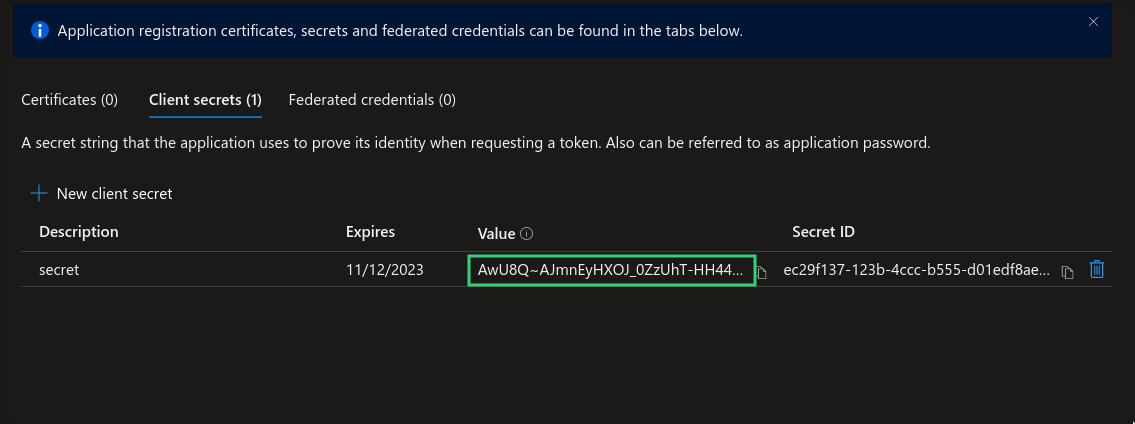
Client Secret
Authentication key for your registered application.
Steps to generate:
Access secret creation
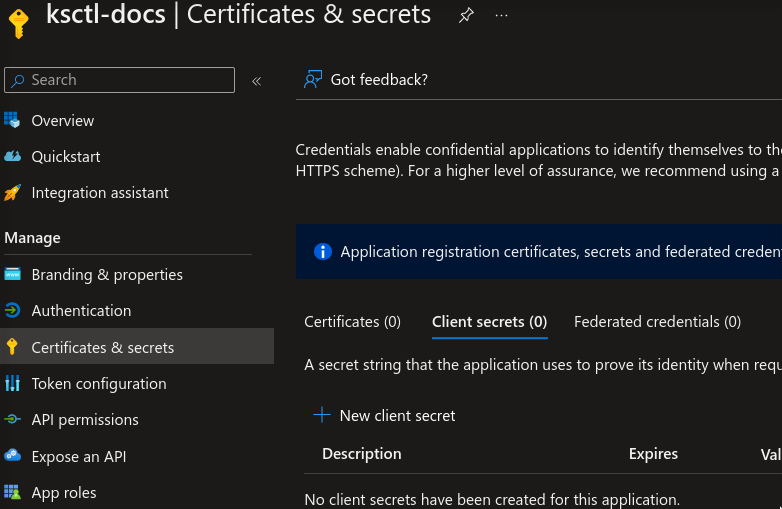
Configure secret settings
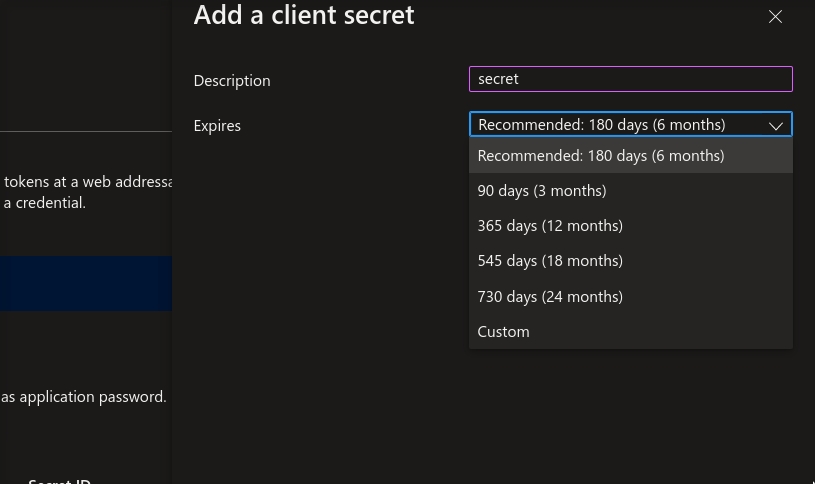
Save the generated secret
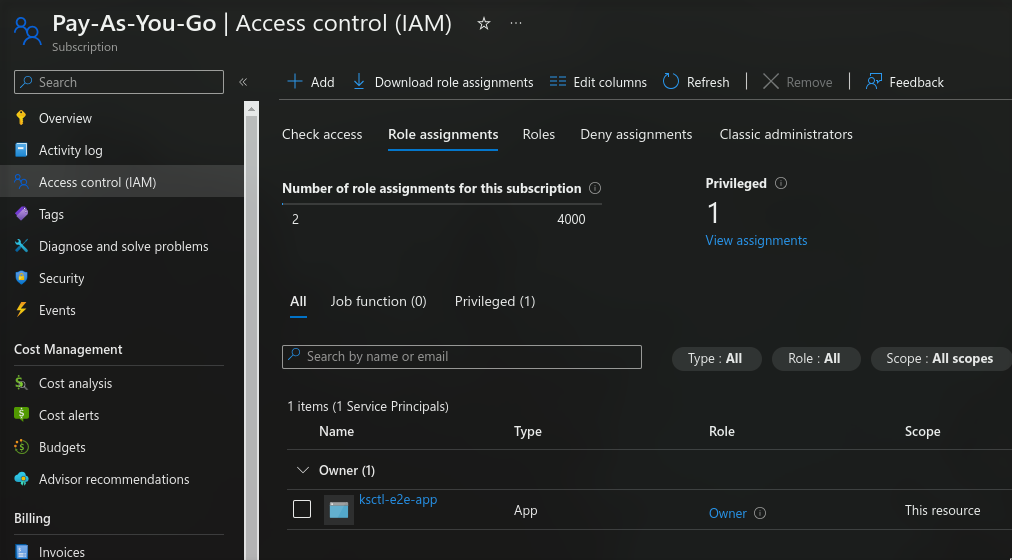
Role Assignment
Configure application permissions:
- Navigate to Subscriptions > Access Control (IAM)
- Select “Role Assignment”
- Click “Add > Add Role Assignment”
- Create new role and specify the application name
- Configure desired permissions
You can create a custom Role and then attach to this app if you want fine grained permission Beta
{
"properties": {
"roleName": "Ksctl",
"description": "Kubmin.ksctl.com",
"assignableScopes": [
"/subscriptions/<subscription_id>"
],
"permissions": [
{
"actions": [
"Microsoft.ContainerService/register/action",
"Microsoft.ContainerService/unregister/action",
"Microsoft.ContainerService/operations/*",
"Microsoft.ContainerService/managedClusters/*",
"Microsoft.ContainerService/managedclustersnapshots/*",
"Microsoft.ContainerService/containerServices/*",
"Microsoft.ContainerService/deploymentSafeguards/*",
"Microsoft.ContainerService/locations/*",
"Microsoft.ContainerService/snapshots/*",
"Microsoft.Network/register/action",
"Microsoft.Network/unregister/action",
"Microsoft.Network/checkTrafficManagerNameAvailability/action",
"Microsoft.Network/internalNotify/action",
"Microsoft.Network/getDnsResourceReference/action",
"Microsoft.Network/queryExpressRoutePortsBandwidth/action",
"Microsoft.Network/checkFrontDoorNameAvailability/action",
"Microsoft.Network/privateDnsZonesInternal/action",
"Microsoft.Network/adminNetworkSecurityGroups/*",
"Microsoft.Network/applicationGateways/*",
"Microsoft.Network/ApplicationGatewayWebApplicationFirewallPolicies/*",
"Microsoft.Network/applicationGatewayAvailableRequestHeaders/*",
"Microsoft.Network/applicationGatewayAvailableResponseHeaders/*",
"Microsoft.Network/applicationGatewayAvailableServerVariables/*",
"Microsoft.Network/applicationGatewayAvailableSslOptions/*",
"Microsoft.Network/applicationGatewayAvailableWafRuleSets/read",
"Microsoft.Network/applicationSecurityGroups/*",
"Microsoft.Network/operations/*",
"Microsoft.Network/azurefirewalls/*",
"Microsoft.Network/azureFirewallFqdnTags/read",
"Microsoft.Network/dnsResolvers/*",
"Microsoft.Network/dnszones/*",
"Microsoft.Network/dnsoperationresults/*",
"Microsoft.Network/firewallPolicies/*",
"Microsoft.Network/gatewayLoadBalancerAliases/*",
"Microsoft.Network/ipAllocations/*",
"Microsoft.Network/ipGroups/*",
"Microsoft.Network/loadBalancers/*",
"Microsoft.Network/natGateways/*",
"Microsoft.Network/networkInterfaces/*",
"Microsoft.Network/virtualNetworks/*",
"Microsoft.Network/virtualNetworkGateways/read",
"Microsoft.Network/virtualNetworkGateways/write",
"Microsoft.Network/virtualNetworkGateways/delete",
"microsoft.network/virtualnetworkgateways/*",
"Microsoft.Network/virtualRouters/*",
"Microsoft.Resources/checkResourceName/action",
"Microsoft.Resources/changes/*",
"Microsoft.Resources/deployments/*",
"Microsoft.Resources/deploymentScripts/*",
"Microsoft.Resources/deploymentStacks/*",
"Microsoft.Resources/locations/*",
"Microsoft.Resources/providers/*",
"Microsoft.Resources/links/*",
"Microsoft.Resources/resources/*",
"Microsoft.Resources/subscriptions/*",
"Microsoft.Resources/subscriptions/locations/*",
"Microsoft.Resources/subscriptions/resourceGroups/*",
"Microsoft.Resources/subscriptions/providers/*",
"Microsoft.Resources/subscriptions/operationresults/*",
"Microsoft.Resources/subscriptions/resources/*",
"Microsoft.Resources/subscriptions/tagNames/*",
"Microsoft.Resources/subscriptionRegistrations/*",
"Microsoft.Resources/tags/*",
"Microsoft.Resources/templateSpecs/*",
"Microsoft.Resources/templateSpecs/versions/*",
"Microsoft.Resources/tenants/*",
"Microsoft.ManagedIdentity/register/*",
"Microsoft.ManagedIdentity/operations/*",
"Microsoft.ManagedIdentity/identities/*",
"Microsoft.ManagedIdentity/userAssignedIdentities/*"
],
"notActions": [],
"dataActions": [],
"notDataActions": []
}
]
}
}
Authentication Methods
Command Line Interface
ksctl configure cloud
Available Cluster Types
Self-Managed Clusters
Self-managed clusters with the following components:
- Distributed etcd database instances
- HAProxy load balancer for control plane high availability
- Multiple control plane nodes
- Worker nodes
Bootstrap options:
- k3s (lightweight Kubernetes distribution)
- kubeadm (official Kubernetes bootstrap tool)
Azure Kubernetes Service (AKS)
Fully managed Kubernetes service by Azure.
Cluster Management Features
Cluster Operations
Managed Clusters (AKS)
- Create and delete operations
- Cluster switching
- Infrastructure updates currently not supported
High Availability Clusters
- Worker node scaling (add/remove)
- Secure SSH access to all components:
- Database nodes
- Load balancer
- Control plane nodes
- Worker nodes
- Protected by SSH key authentication
- Public access enabled
Looking for CLI Commands?
All CLI commands mentioned in this documentation have detailed explanations in our command reference guide.
CLI Reference
👉 Check out our comprehensive CLI Commands Reference for:
- Detailed command syntax
- Usage examples
- Available options and flags
- Common use cases
3 - Kind
It creates cluster on the host machine utilizing kind
Note
Prequisites: DockerCurrent features
currently using Kind Kubernetes in Docker
Looking for CLI Commands?
All CLI commands mentioned in this documentation have detailed explanations in our command reference guide.
CLI Reference
👉 Check out our comprehensive CLI Commands Reference for:
- Detailed command syntax
- Usage examples
- Available options and flags
- Common use cases