This Page includes more info about different cloud providers
This is the multi-page printable view of this section. Click here to print.
Cloud Provider
- 1: Amazon Web Services
- 2: Azure
- 3: Civo
- 4: Google Cloud Platform
- 5: Local
1 - Amazon Web Services
Aws support for HA and Managed Clusters
Caution
we need credentials to access clusters
these are confidential information so shouldn’t be shared with anyone
How these credentials are used by ksctl
- Environment Variables
export AWS_ACCESS_KEY_ID=""
export AWS_SECRET_ACCESS_KEY=""
- Using command line
ksctl cred
Current Features
Cluster features
Highly Available cluster
clusters which are managed by the user not by cloud provider
you can choose between k3s and kubeadm as your bootstrap tool
custom components being used
- Etcd database VM
- HAProxy loadbalancer VM for controlplane nodes
- controlplane VMs
- workerplane VMs
Managed Cluster Elastic Kubernetes Service
we provision Roles ksctl-* 2 for each cluster:
ksctl-<clustername>-wp-rolefor the EKS NodePoolksctl-<clustername>-cp-rolefor the EKS controlplane
we utilize the iam:AssumeRole to assume the role and create the cluster
Policies aka permissions for the user
here is the policy and role which we are using
- iam-role-full-access(Custom Policy)
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor6",
"Effect": "Allow",
"Action": [
"iam:CreateInstanceProfile",
"iam:DeleteInstanceProfile",
"iam:GetRole",
"iam:GetInstanceProfile",
"iam:RemoveRoleFromInstanceProfile",
"iam:CreateRole",
"iam:DeleteRole",
"iam:AttachRolePolicy",
"iam:PutRolePolicy",
"iam:ListInstanceProfiles",
"iam:AddRoleToInstanceProfile",
"iam:ListInstanceProfilesForRole",
"iam:PassRole",
"iam:CreateServiceLinkedRole",
"iam:DetachRolePolicy",
"iam:DeleteRolePolicy",
"iam:DeleteServiceLinkedRole",
"iam:GetRolePolicy",
"iam:SetSecurityTokenServicePreferences"
],
"Resource": [
"arn:aws:iam::*:role/ksctl-*",
"arn:aws:iam::*:instance-profile/*"
]
}
]
}
- eks-full-access(Custom Policy)
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"eks:ListNodegroups",
"eks:ListClusters",
"eks:*"
],
"Resource": "*"
}
]
}
- AmazonEC2FullAccess(Aws)
- IAMReadOnlyAccess(Aws)
Validaty of Kubeconfig
The Kubeconfig generated after you ran
ksctl switch aws --name here-you-go --region us-east-1
we are using sst token to authenticate with the cluster, so the kubeconfig is valid for 15 minutes
once you see that there is a error of unauthorized then you need to re-run the above command
2 - Azure
Azure support for HA and Managed Clusters
Caution
we need credentials to access clusters
these are confidential information so shouldn’t be shared with anyone
Azure Subscription ID
subscription id using your subscription
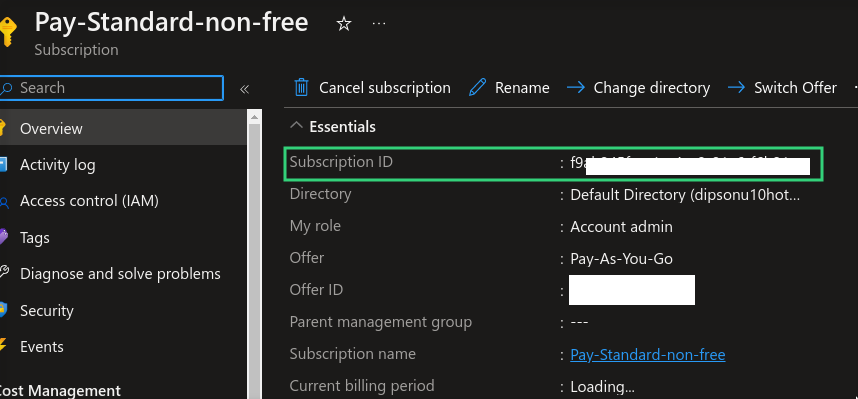
Azure Tenant ID
Azure Dashboard
Azure Dashboard contains all the credentials required
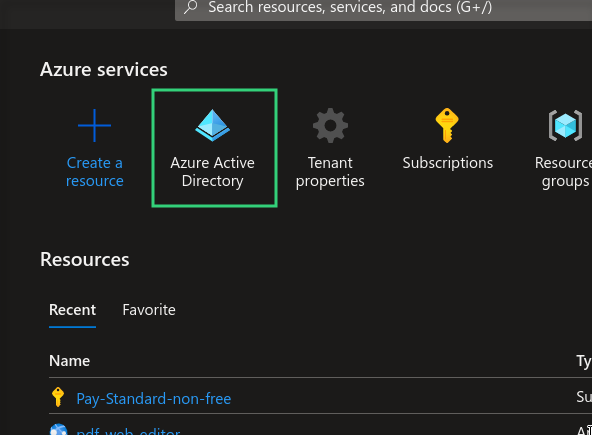
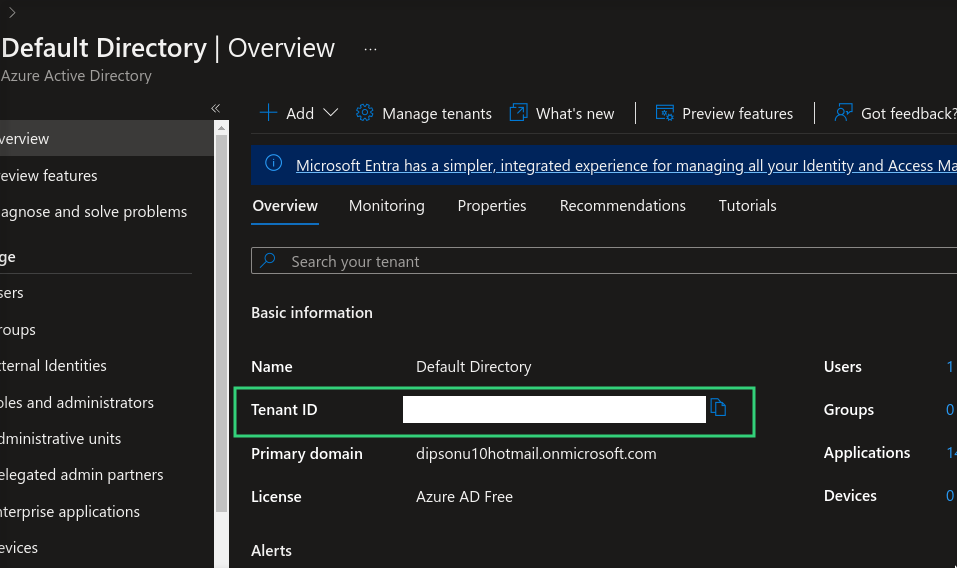
lets get the tenant id from the Azure
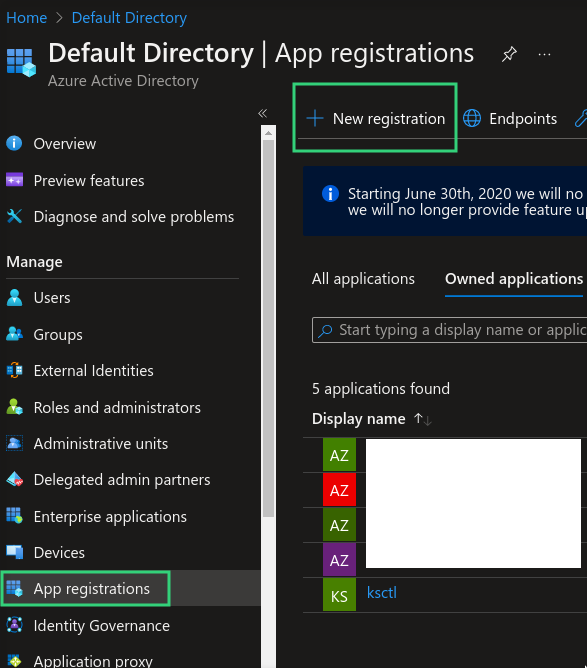
Azure Client ID
it represents the id of app created
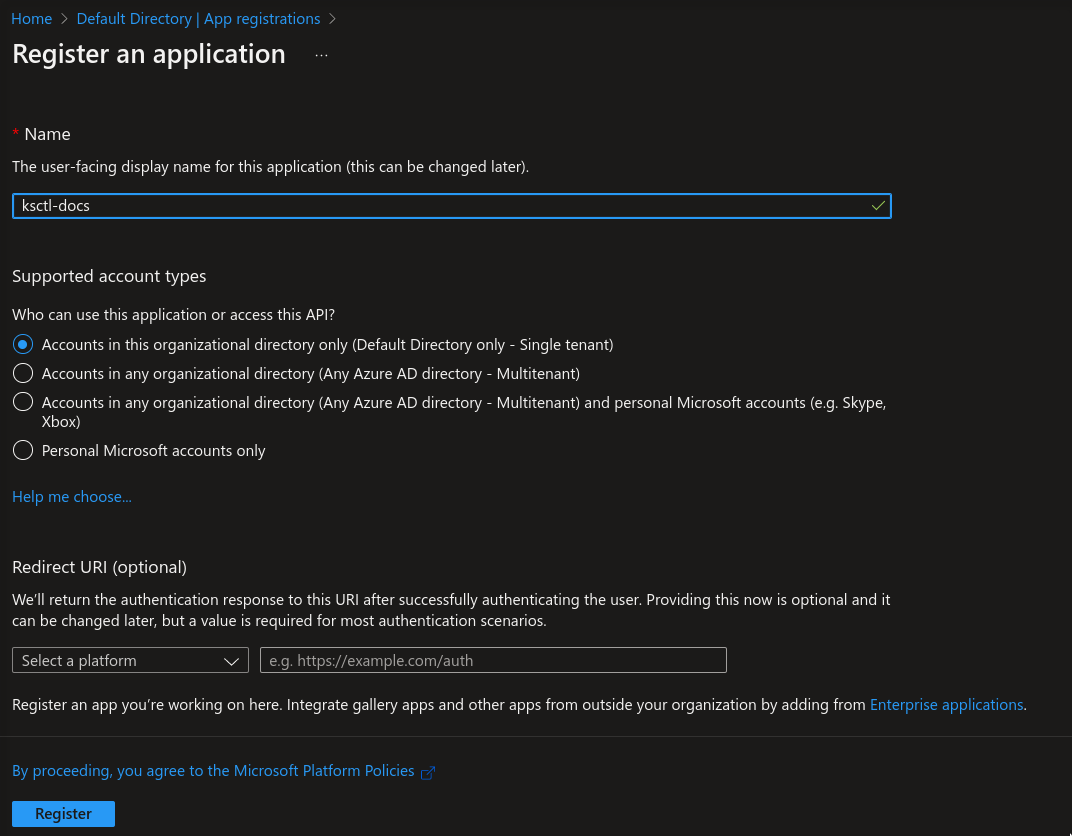
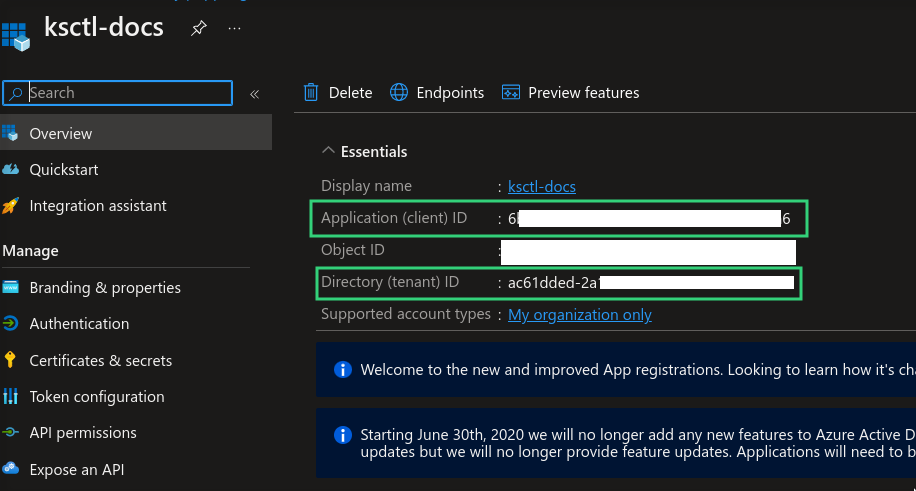
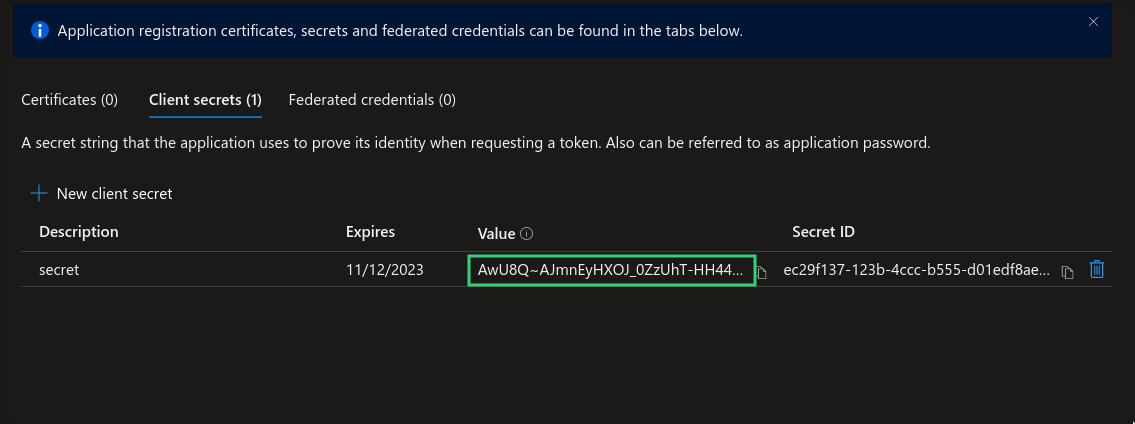
Azure Client Secret
it represents the secret associated with the app in order to use it
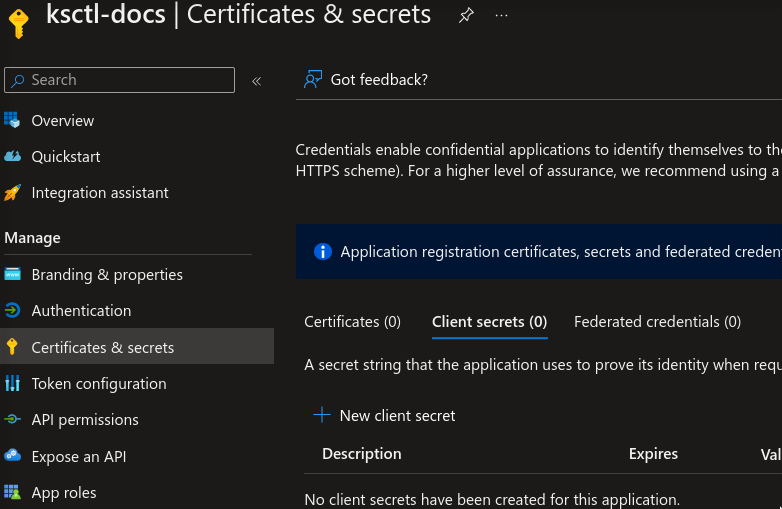
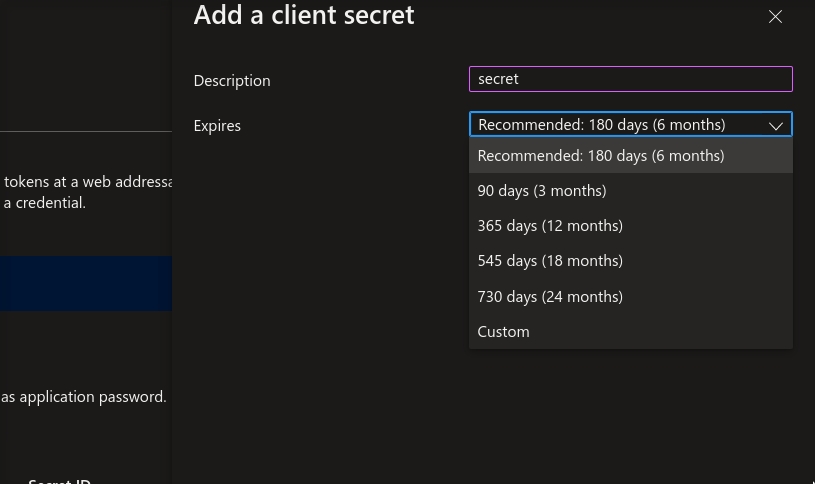
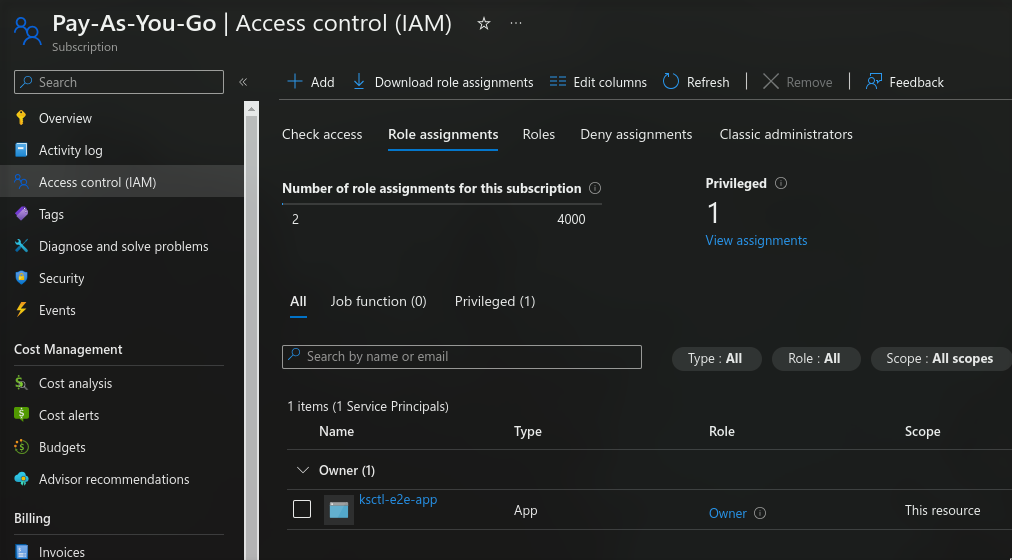
Assign Role to your app
head over to subscriptions page and click Access Control (IAM) select the Role Assignment and then click Add > Add Role Assignment create a new role and when selecting the identity specify the name of the app Here you can customize the role this app has
How these credentials are used by ksctl
- Environment Variables
export AZURE_TENANT_ID=""
export AZURE_SUBSCRIPTION_ID=""
export AZURE_CLIENT_ID=""
export AZURE_CLIENT_SECRET=""
- Using command line
ksctl cred
Current Features
Cluster features
Highly Available cluster
clusters which are managed by the user not by cloud provider
you can choose between k3s and kubeadm as your bootstrap tool
custom components being used
- Etcd database VM
- HAProxy loadbalancer VM for controlplane nodes
- controlplane VMs
- workerplane VMs
Managed Cluster
clusters which are managed by the cloud provider
Other capabilities
Create, Update, Delete, Switch
Update the cluster infrastructure
Managed cluster: till now it’s not supported
HA cluster
- addition and deletion of new workerplane node
- SSH access to each cluster node (DB, LB, Controplane, WorkerPlane) Public Access, secured by private key
3 - Civo
Civo support for HA and Managed Clusters
Caution
we need credentials to access clusters
these are confidential information so shouldn’t be shared with anyone
Getting credentials
under settings look for the profile
copy the credentials
How to add credentials to ksctl
- Environment Variables
export CIVO_TOKEN=""
- Using command line
ksctl cred
Current Features
Cluster features
Highly Available cluster
clusters which are managed by the user not by cloud provider
you can choose between k3s and kubeadm as your bootstrap tool
custom components being used
- Etcd database VM
- HAProxy loadbalancer instance for controlplane nodes
- controlplane instances
- workerplane instances
Managed Cluster
clusters which are managed by the cloud provider
Other capabilities
Create, Update, Delete, Switch
Update the cluster infrastructure
Managed cluster: till now it’s not supported
HA cluster
- addition and deletion of new workerplane node
- SSH access to each cluster node (DB, LB, Controplane) Public Access, secured by private key
- SSH access to each workplane Private Access via local network, secured by private key
4 - Google Cloud Platform
Gcp support for HA and Managed Clusters
Caution
we need credentials to access clusters
these are confidential information so shouldn’t be shared with anyone
5 - Local
It creates cluster on the host machine utilizing kind
Note
Prequisites: DockerCurrent features
currently using Kind Kubernetes in Docker